Things relevant to my interest, and maybe yours.
Nostalgie Timeline
Computer
Hardware
- 1991 - Hiscreen 386sx 16MHz - 1MB RAM - 40MB HDD ca 3000DM


- 1993-04-17 1MB RAM + Ultima VII (Miami)
- 1994 - IBM PS/1 Model 2168 - iirc: 486DX2 66MHz - 4MB RAM
- 1995+ - Matrox Mystique
- 1996+ - Voodoo
- 1996+ - Cyrix 6x86 266MHz?
- 1998+ - Celeron-400-mendocino Slot 1

- 1999+ - Nvidia Riva TNT2 + Video out und Tuner/Video grabber (Premiere)
- 2002+ - AMD Athlon XP 1800+ @ ASUS A7N8X-E (nforce2)
- 2002+ - GeForce4 Ti4200 @ AGP ?
Software
- 1991 DR-DOS 5.0 + Windows 3.0
- Ultima VI
- Wing Commander
- 1995+ PTS-DOS 6.51CD?
- 1998 SuSe Linux 5.2
- 2002 Gentoo 1.2
- 2003-02-05 join forum.gentoo.org
- 2006?? Arch Linux
- 20XX Debian
- 2019 Gentoo
Thanks to prof_braino I elaborate a bit about my spinneret setup:
I'll try to explain On the network side things are simple. Netmask for ALL is /24 aka 255.255.255.0, gateway for all but the router is the router's IP 192.168.1.1 The core components are:
- A Router setup as 192.168.1.1 (providing dhcp for the 192.168.1.100+ Range)
- My Qnap NAS/Server (castle) setup with a static 192.168.1.10
- The Spinneret is configured at 192.168.1.5
- My Notebook via Wlan 192.168.1.23
It's the easiest way to let the spinneret be a part of your "real" net, as long as its private and you have a router, there are only very few security concerns. Having it this way there is no need at all to modify your routing or your IP addresses.
Some ports are forwarded to the server (22,80 ...) also I can enable a port forwarding to the spinneret from the outside world if the need should arise, but as I have no authentication implemented in propforth nor is there any cryptography available, that's not always on.
At the Moment the Spinneret is fed by the Qnap server itself via USB shared with the propplug. So the develpement can be done completely remote. The main feature is the connection of Pin 26 and 27 to the native UART on the Mainboard of the QNAP. (you can find details in the links on my blog entry). Normally that UART is not meant to be used by the customer, so One need to open up the Case to get Debian running and anytime net access fails for whatever reason. Having an out-of-band management available is a real nice to have.
A few words about the remote programming: As there are very few tools available to get things onto the propeller for an ARM enviroment and pyloader failed for some reason, I was on the hunt for some comfy solution. Netcat or socat came in mind to tunnel the serial communication over the net, which works fine for "normal" data, but it turned out the timing needed by the loaders (bst, propellent, you name it) is much to harsh for my trusty "*cats" so I found usbip to be quite a sharp sword for that situation. It basically takes the Propplug (FTDI) from the USB Stack of the Server (QNAP) and let it pop up on the client side (my Laptop) which shows the FTDI Device right in dmesg so I had a locally available /dev/ttyUSB0 to work with. Made me quite happy. I had some fear to get things together on the software side but after I decided to give propforth a try it really was just a walkt hrough the tests (now tutorial) and giving the thing a serial cog and some (ioconn) and ... done. Actually I was even a bit frustrated to see my plans of a week full of propeller coding gone in just an evening of propforth.
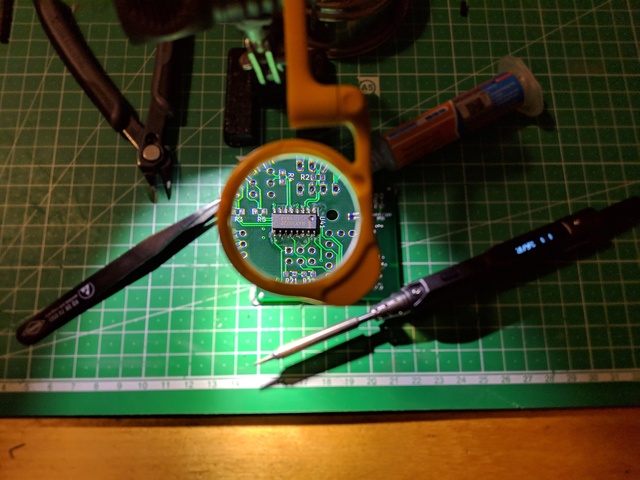
At first some Soldering:
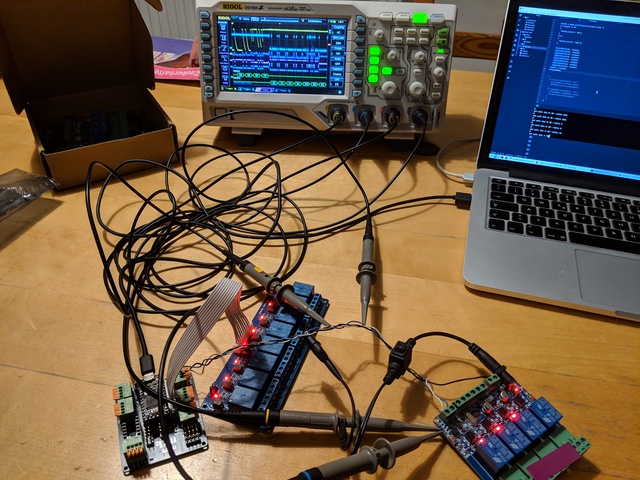
Then heavy testing:
Differential signals are a perfect opportunity to max out the Rigol. Ch 1: TX Ch 2: RX Ch 3: RS484- A Ch 4: RS485+ B Math: A-B Decode1: TX+RX
Luckily my initial Problems tuned out to be soft ones.
For now my new Version is much more usable.
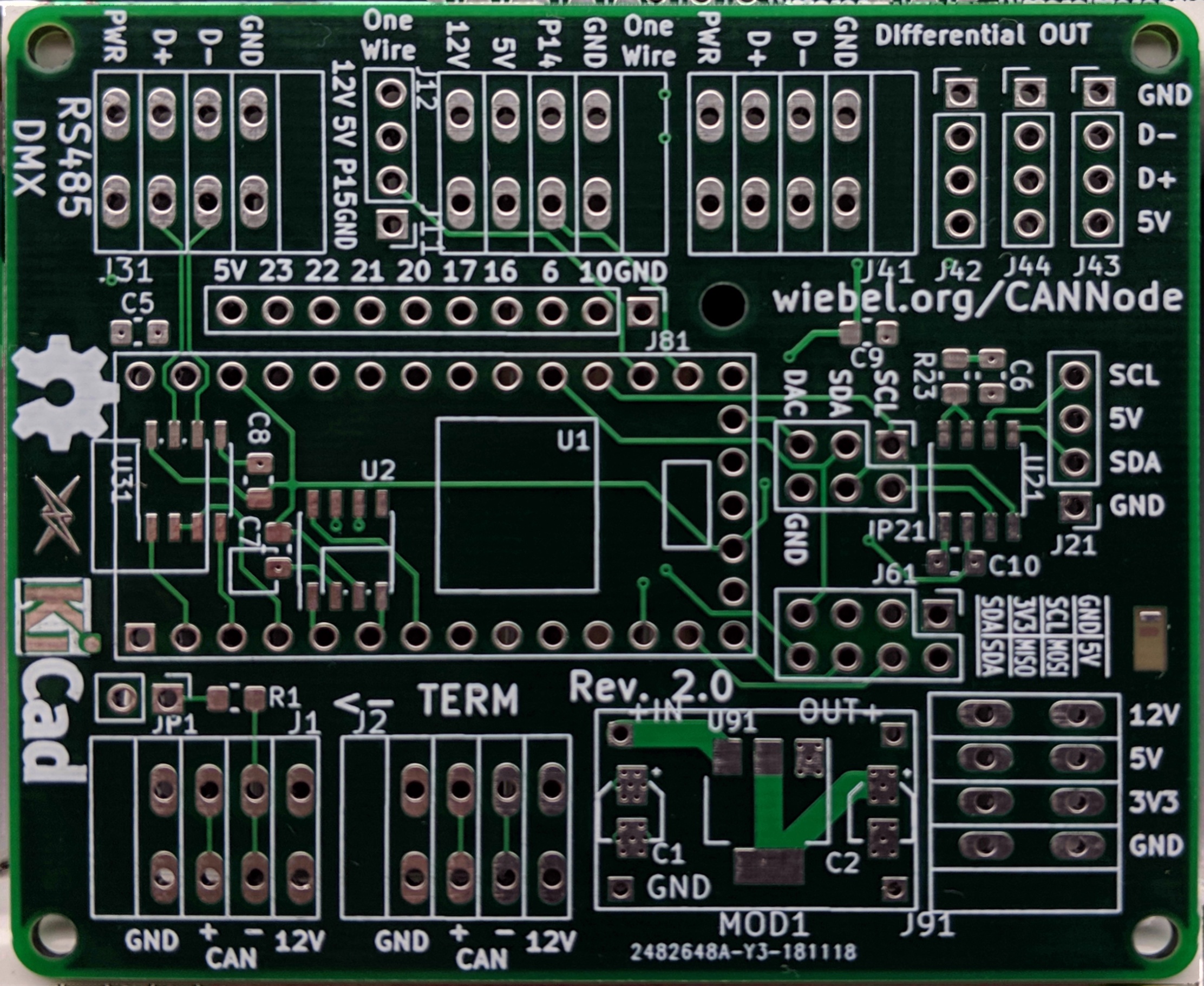
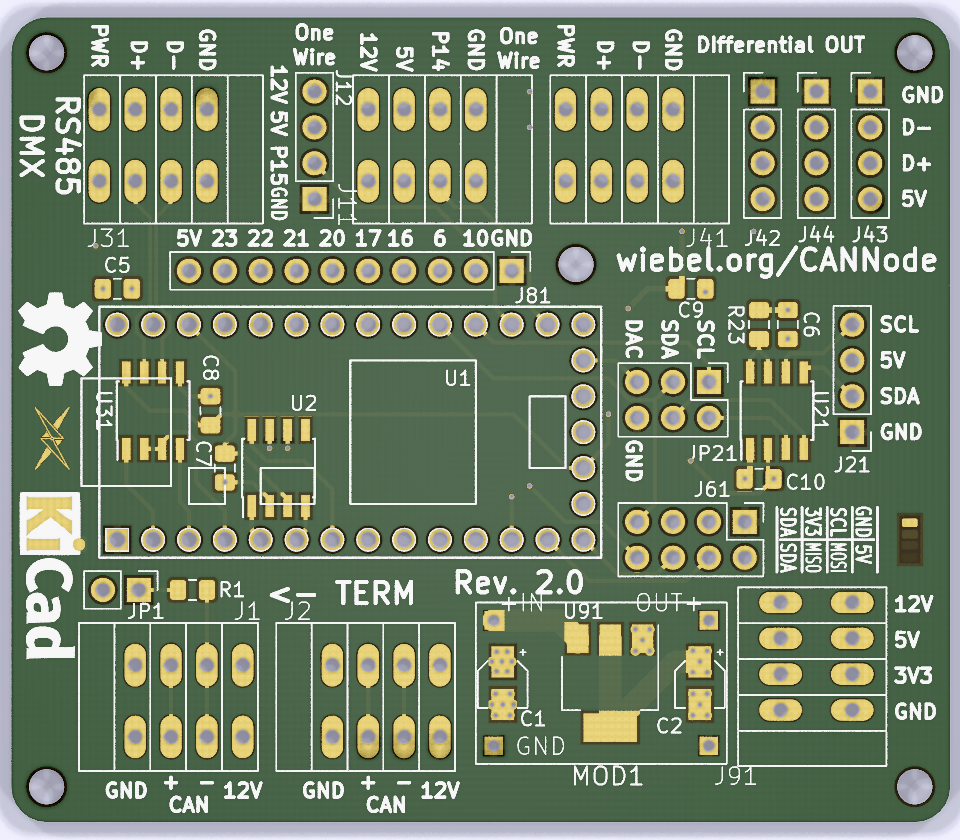
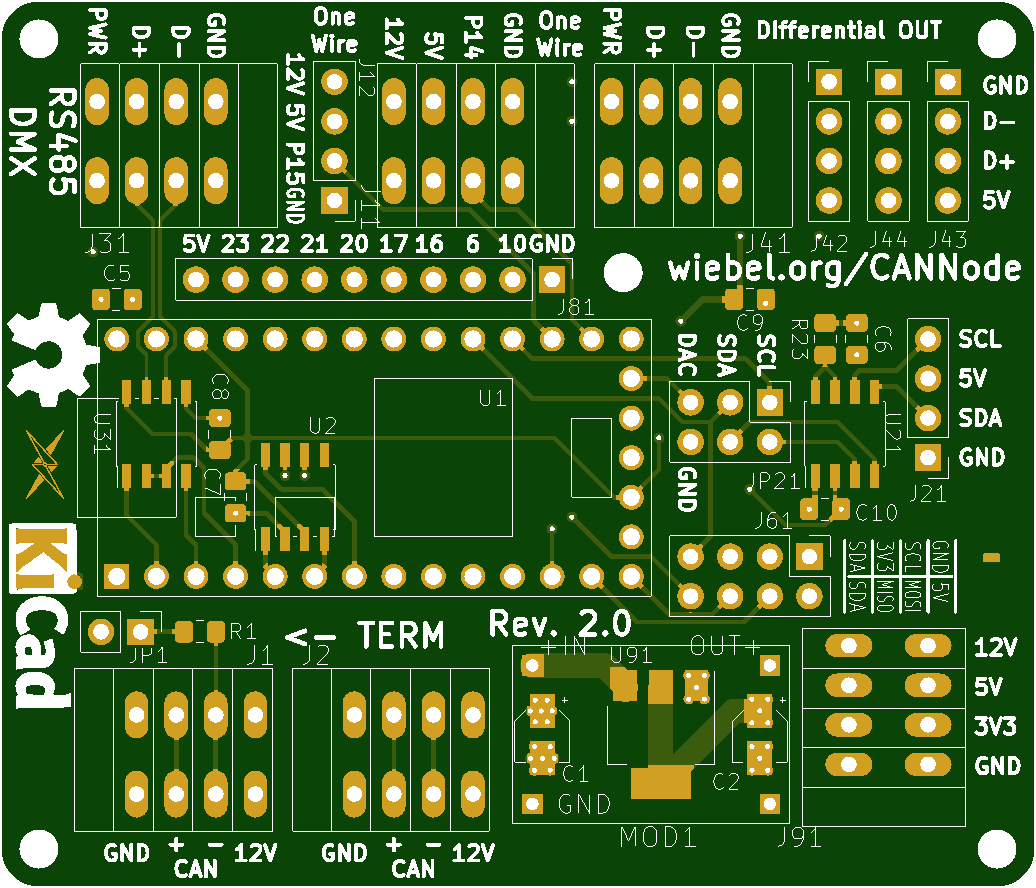
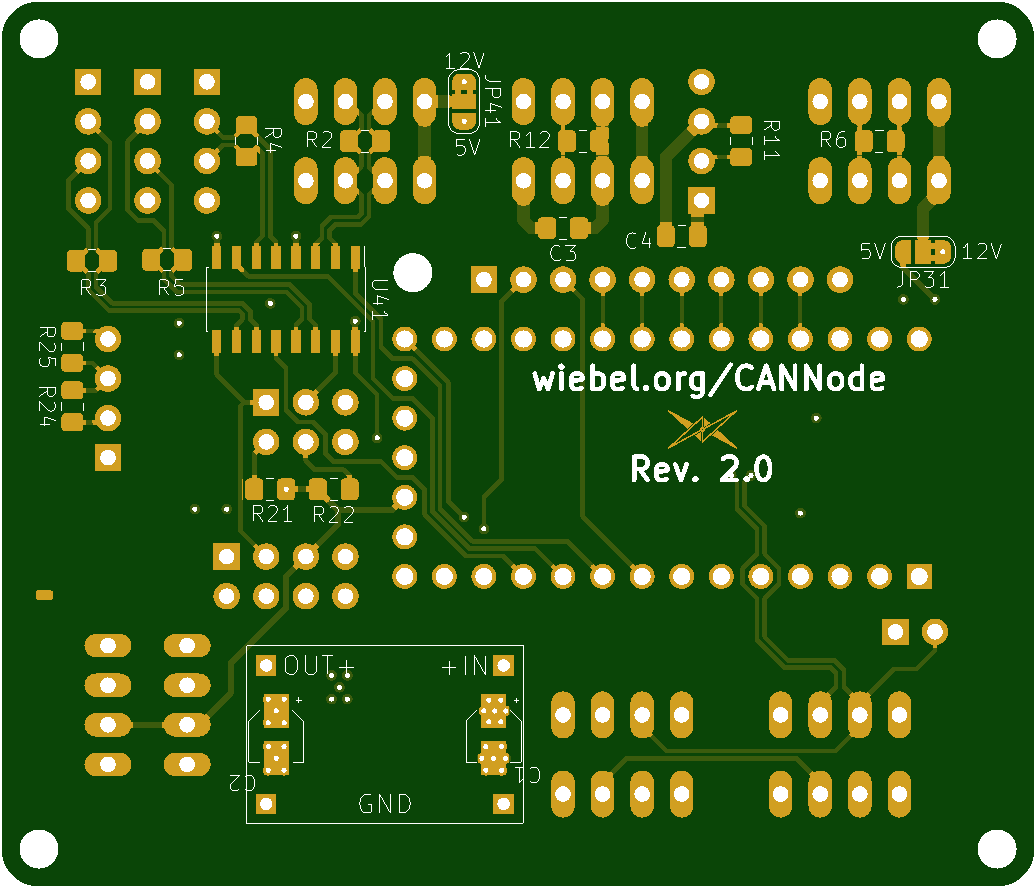
A CAN Node for Home Automation
PCB:
Sources:

This work is licensed under a Creative Commons Attribution-ShareAlike 3.0 Unported License
At first some Soldering:
Then heavy testing:
Differential signals are a perfect opportunity to max out the Rigol. Ch 1: TX Ch 2: RX Ch 3: RS484- A Ch 4: RS485+ B Math: A-B Decode1: TX+RX
Luckily my initial Problems tuned out to be soft ones.
For now my new Version is much more usable.
Posted
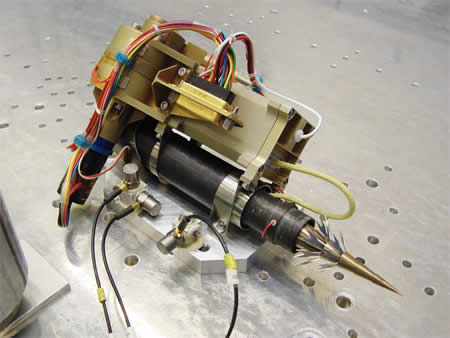
That's what Rosetta will fire at poor ol' Churyumov–Gerasimenko in November, any other Duck might be scared. Remember all the technology has been launched Years before the first Smartphone. Mankind has come quite a long way.
On Max-Planck-Institut für extraterrestrische Physik is a very detailed (german) Presentation.
Further Informations from the Manufacturer: Faulhaber
See it in action : Scientists Test Harpoon Used in Rosetta Probe
Anzahl Mails in Queue:
exim -bpc
Listing der Queue:
exim -bpr
Suchen in der Queue: siehe exiqgrep -h
Beispiel: Alle Frozen Mails loeschen
exiqgrep -z -i | xargs exim -Mrm
To delete all queued messages containing a certain string in the body:
grep -lr 'a certain string' /var/spool/exim/input/ | \
sed -e 's/^.*\/\([a-zA-Z0-9-]*\)-[DH]$//g' | xargs exim -Mrm
T-Shirt inspired by the web
.. esp. ThinkGeek
The font (if I might call it so) was truthfully copied from my trusty HP32s.
The svgs are outlined so a cutter should be able to parse it.
Front:
Back:
Home
Home
Tidy ACLs listings on ASA
Normaly a show access-list would bring up something like
access-list OUTSIDE-IN line 1 extended permit ip object-group FOO any (hitcnt=9001)
access-list OUTSIDE-IN line 1 extended permit ip host 10.42.23.1 any (hitcnt=9000)
access-list OUTSIDE-IN line 1 extended permit ip host 10.42.23.2 any (hitcnt=1)
access-list OUTSIDE-IN line 1 extended permit ip host 10.42.23.3 any (hitcnt=0)
access-list OUTSIDE-IN line 1 extended permit ip host 10.42.23.4 any (hitcnt=0)
access-list OUTSIDE-IN line 1 extended permit ip host 10.42.23.5 any (hitcnt=0)
access-list OUTSIDE-IN line 1 extended permit ip host 10.42.23.6 any (hitcnt=0)
access-list OUTSIDE-IN line 1 extended permit ip host 10.42.23.7 any (hitcnt=0)
access-list OUTSIDE-IN line 2 extended permit ip object-group BAR any (hitcnt=9002)
...
Sometimes you just like to see the leading configuration lines. To get there you can simply exclude a double whitespace like:
show access-list | exclude \ \
access-list OUTSIDE-IN line 1 extended permit ip object-group FOO any (hitcnt=9001)
access-list OUTSIDE-IN line 2 extended permit ip object-group BAR any (hitcnt=9002)
The algorithm consistently finds Jesus.
The algorithm killed Jeeves.
The algorithm is banned in China.
The algorithm is from Jersey.
The algorithm constantly finds Jesus.
This is not the algorithm.
This is close.
This wiki is powered by ikiwiki.